Kubernetes Ingress vs Load Balancer: When to Use Each
TL;DR
- Pick Ingress for HTTP/HTTPS routing to multiple Services behind one entry point and one load balancer.
- Pick Service Type
LoadBalancerfor simple L4 exposure to a single Service, low latency, or when you don’t need host/path routing. - Consider Gateway API if you want role-oriented, multi-protocol routing and cleaner separation of duties.
Table of contents will auto-insert here.
What’s the difference between a Kubernetes Ingress and a LoadBalancer Service?
Answer (featured-snippet length):
An Ingress is a Kubernetes API object for HTTP/HTTPS routing that relies on an Ingress controller (a proxy) to map hosts/paths to Services. A Service Type LoadBalancer asks your cloud to provision an external L4 load balancer for one Service endpoint. Use Ingress for multi-service web routing; use LoadBalancer for simple L4 exposure. Kubernetes+1
Definitions
Ingress (L7 HTTP/S routing)
An API object that manages external access—typically HTTP(S)—and can provide path/host routing, TLS termination, and name-based virtual hosting, implemented by an Ingress controller such as NGINX or Traefik. Kubernetes+1
Service Type LoadBalancer (L4)
A Kubernetes Service that, when supported by the environment, provisions a cloud load balancer with a public IP/DNS and forwards connections to the target Service’s node ports. Kubernetes+1
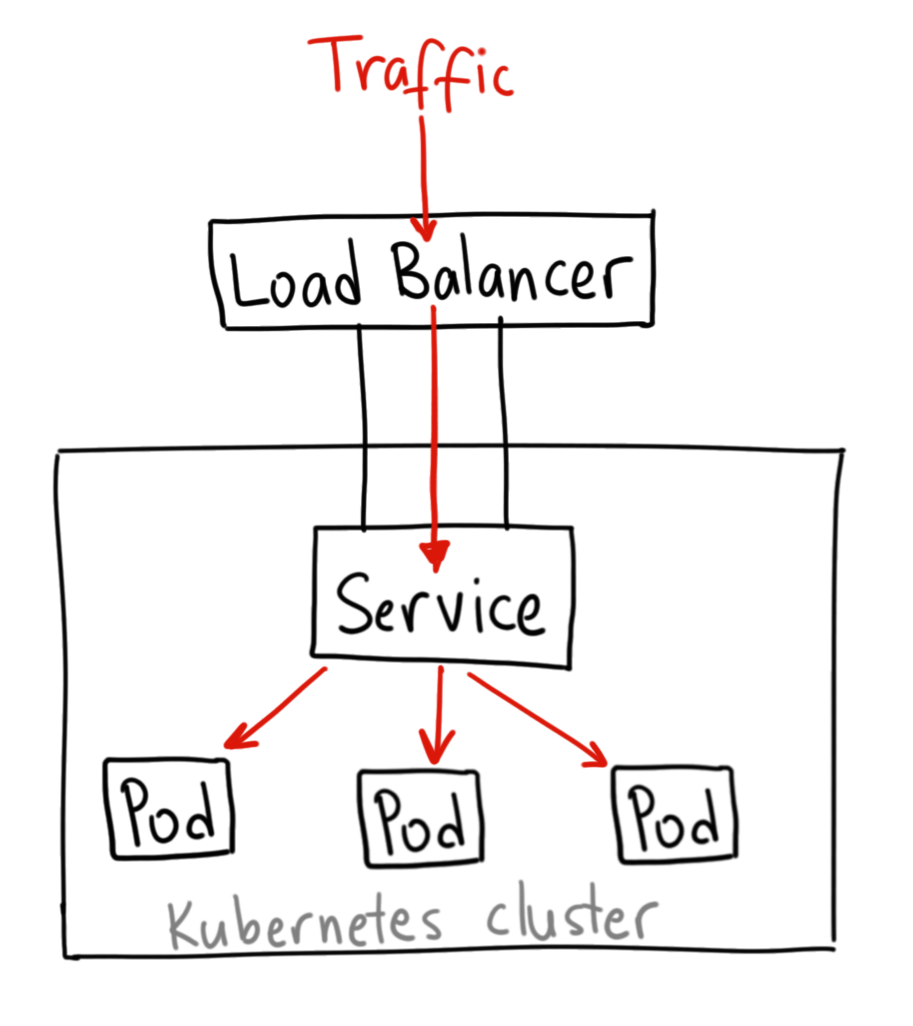
How each one works (diagram)
Alt text: “Diagram showing two patterns: A) Ingress with one external LB feeding an Ingress controller that routes to multiple Services; B) Service Type LoadBalancer creating a cloud LB per Service.”
[Internet] | | (A) Ingress pattern (L7) v [ Cloud/External LB ] --> [ Ingress Controller (e.g., NGINX/Traefik) ] | \ [svc A] [svc B] | | [pods] [pods] | (B) LoadBalancer Service (L4) v [ Cloud LB ] --> [svc X] --> [pods]
- In major clouds (e.g., AWS), an Ingress often results in an Application Load Balancer (ALB), while a
LoadBalancerService often yields a Network (or Classic) Load Balancer. Controller behavior and annotations decide specifics. AWS Documentation+1
Where it’s used (3 scenarios)
- Many web microservices behind one entry point
Use Ingress to mapapi.example.comand/shop/*to different backends without creating many cloud load balancers. Kubernetes - Low-latency TCP services
Use Service TypeLoadBalancerfor L4 protocols (MQTT, gRPC on 80/443 terminated elsewhere, databases in dev) when you don’t need host/path routing. Kubernetes - Edge-first / zero-egress clusters
Use an edge provider (e.g., Cloudflare Tunnel) to avoid opening inbound ports and still expose Services via a managed edge. This can complement or replace an in-cluster Ingress. Cloudflare Docs
Trade-offs & misconceptions
- “Ingress replaces load balancers.”
Not exactly. The controller typically runs on a Service that itself may be backed by a load balancer; the Ingress defines L7 rules. Kubernetes - Protocol scope:
Core Ingress targets HTTP(S).LoadBalanceris L4. For richer multi-protocol control, evaluate Gateway API (HTTPRoute, GRPCRoute, TCPRoute, etc.). Kubernetes - Cost model:
ManyLoadBalancerServices can create many cloud LBs. Ingress can consolidate multiple routes behind one entry point (often one LB), reducing per-LB cost in some setups. (Exact pricing varies by provider.) Kubernetes
Evaluation criteria (weights)
- Routing & protocol flexibility (30%)
- Operational simplicity (20%)
- Performance & latency (20%)
- Security & TLS management (15%)
- Portability & ecosystem support (15%)
At-a-glance comparison
CriterionIngress (with controller)Service Type LoadBalancerProtocolsHTTP/S (core); controller-specific extrasL4 (TCP/UDP)Routes per entryMany (hosts/paths to many Services)One Service per LBTLSTermination at controller; SNI, cert mgmtOften pass-through; TLS usually handled by app or external LBCloud couplingLower (controller is portable)Higher (cloud-provisioned LB)Ops complexityController lifecycle + rulesMinimal YAML; per-Service LBTypical useWeb gateways/multiple appsSimple externalization, low-latency L4
Sources: Kubernetes docs on Ingress and Services. Kubernetes+1
Head-to-head by criterion
Routing & protocol flexibility
Ingress gives host/path routing, TLS termination, and advanced rules via controller features. LoadBalancer exposes a single Service at L4. For multi-protocol, Gateway API generalizes routing beyond HTTP. Kubernetes+2Kubernetes+2
Operational simplicity
LoadBalancer is straightforward: set type: LoadBalancer and let the cloud reconcile. Ingress adds controller selection, lifecycle, and class/annotations, but consolidates entry points. Kubernetes+1
Performance & latency
LoadBalancer (e.g., AWS NLB) forwards at L4 with minimal overhead—good for raw throughput/latency. Ingress performs L7 inspection and TLS termination, adding flexibility with small overhead. (Exact numbers vary by controller and cloud.) AWS Documentation
Security & TLS management
Ingress centralizes TLS and policy (mTLS, WAF options with some controllers). LoadBalancer often defers TLS to the app or external LB policy. Controller choice (NGINX, Traefik) determines features. NGINX DocumentationTraefik Docs
Portability & ecosystem
Ingress controllers run anywhere Kubernetes runs. LoadBalancer depends on cloud/provider capabilities, though projects like kind offer local options. Kuberneteskind.sigs.k8s.io
Use-case picks (“If you need A → choose X”)
- Expose multiple HTTP apps behind one DNS name → Ingress.
- Publish a single TCP service with minimal config → Service Type
LoadBalancer. - Standardize multi-protocol routing with cleaner roles → Gateway API. Kubernetes
- Edge-only exposure without opening inbound ports → Cloudflare Tunnel/Load Balancing (pairs well with Ingress or replaces it in some setups). Cloudflare Docs+1
Migration notes
- From many
LoadBalancerServices to one Ingress:
Deploy an Ingress controller (e.g., NGINX, Traefik). Convert each public Service to a backend referenced by Ingress rules. Validate health checks. Consider HTTP-to-HTTPS redirects. Kubernetes - From Ingress to Gateway API:
Perform a one-time conversion (Ingress → HTTPRoute + Gateway/GatewayClass). Introduce controllers that support Gateway API (e.g., Traefik, Istio, vendor controllers). Kubernetes Gateway APITraefik Docs
Pricing at a glance (indicative, not exhaustive)
OptionWhat you pay forNotesIngress + single external LB1 external LB + controller computeConsolidates many apps behind one entry point.Per-Service LoadBalancer1 external LB per ServiceSimpler; cost scales with number of Services.Edge LB (Cloudflare)Per-zone LB add-on, request/health-check tiersUseful for multi-region/multi-cloud and zero-egress models. Cloudflare Docs
Always check your cloud and vendor pricing pages for current rates.
Pros and Cons
Ingress (with controller)
Pros: Consolidated entry point; rich HTTP routing; centralized TLS/policy; portable across clusters.
Cons: Controller ops overhead; L7 adds some latency; non-HTTP workloads need workarounds or Gateway API. Kubernetes
Service Type LoadBalancer
Pros: Minimal config; low L4 overhead; great for single-service publish.
Cons: One LB per Service (cost/quotas); limited routing; cloud coupling. Kubernetes
Quick YAML examples
Service Type LoadBalancer (L4)
apiVersion: v1 kind: Service metadata: name: tcp-app spec: type: LoadBalancer ports: - port: 1883 targetPort: 1883 protocol: TCP selector: app: tcp-app
What you’ll see: a cloud L4 LB with a public address that forwards to tcp-app pods. Kubernetes
Ingress (HTTP routing via NGINX Ingress)
apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: web-gateway annotations: nginx.ingress.kubernetes.io/rewrite-target: / spec: ingressClassName: nginx tls: - hosts: [ "shop.example.com" ] secretName: shop-tls rules: - host: shop.example.com http: paths: - path: /api pathType: Prefix backend: service: name: api-svc port: number: 80 - path: / pathType: Prefix backend: service: name: frontend-svc port: number: 80
What you’ll see: one public entry point routes by host/path to multiple Services; TLS terminates at the controller. kubernetes.github.io
Troubleshooting pointers
- Connections reach the Service but not pods: check selectors and targetPorts; verify health checks.
- Ingress not picking up rules: ensure
ingressClassNameor default class exists; check controller logs. Kubernetes - AWS: wrong LB type created: set the correct annotations/loadBalancerClass for ALB vs NLB under the AWS Load Balancer Controller. AWS Documentationkubernetes-sigs.github.io
Internal links (related pillars)
- Kubernetes networking basics →
/kubernetes-networking-basics/ - Kubernetes Service types explained →
/kubernetes-service-types/ - Ingress controllers compared →
/kubernetes-ingress-controllers/ - Gateway API deep dive →
/kubernetes-gateway-api/ - Zero-trust vs VPN for clusters →
/zero-trust-vs-vpn/
Where to get it (after evaluation)
<div role="complementary" aria-label="Where to get it box"> <ul> <li><a href="https://docs.nginx.com/nginx-ingress-controller/" rel="sponsored nofollow">Start free trial at NGINX</a></li> <li><a href="https://doc.traefik.io/traefik/" rel="sponsored nofollow">See Traefik plans</a></li> <li><a href="https://aws.amazon.com/elasticloadbalancing/" rel="sponsored nofollow">Compare AWS ELB options</a></li> <li><a href="https://www.cloudflare.com/load-balancing/" rel="sponsored nofollow">See Cloudflare Load Balancing</a></li> <li><a href="https://kubernetes.io/docs/concepts/services-networking/ingress/" rel="nofollow">Read the Kubernetes Ingress docs (non-affiliate)</a></li> </ul> </div>
FAQ
Is Ingress required to expose apps publicly?
No. A LoadBalancer Service can expose a single Service directly. Ingress becomes valuable when you need L7 routing, TLS centralization, or one entry point for many apps. Kubernetes+1
What Ingress controller should the site recommend?
NGINX and Traefik are mature, widely supported, and document feature sets clearly. Choose NGINX for deep NGINX ecosystem features; choose Traefik for CRD-first workflows and Gateway API support. NGINX DocumentationTraefik Docs
What about the Gateway API—does it replace Ingress?
Gateway API is the successor to Ingress for many cases and offers broader protocol coverage and role-oriented design. Many controllers support both; migration is incremental. KubernetesKubernetes Gateway API
Sources & further reading
- Kubernetes Ingress & Service docs: Ingress; Service; create external load balancer; ingress controllers. Kubernetes+3Kubernetes+3Kubernetes+3
- Controllers: NGINX Ingress Controller; Traefik Kubernetes Ingress. NGINX DocumentationTraefik Docs
- Cloud specifics: AWS Load Balancer Controller guide; EKS best practices; GKE LoadBalancer Service parameters; Cloudflare Load Balancing docs. AWS Documentation+1Google CloudCloudflare Docs
- Gateway API: Intro and migration. KubernetesKubernetes Gateway API
- UX/SEO/Accessibility standards: Google helpful content; Schema.org Article; NNGroup scannability; Web Vitals; WCAG. Google for DevelopersSchema.orgNielsen Norman Groupweb.devW3C
- FTC Endorsement Guides: overview and FAQ. Federal Trade Commission+1
Compliance & metadata
- Keyword placement: present in H1, intro, H2, alt text, and naturally throughout.
- Schema (Article):
<!-- Canonical for “vs” pages --> <link rel="canonical" href="https://example.com/kubernetes-ingress-vs-load-balancer/" /> <script type="application/ld+json"> { "@context":"https://schema.org", "@type":"Article", "headline":"Kubernetes Ingress vs Load Balancer: When to Use Each", "description":"Learn the difference between Kubernetes Ingress and LoadBalancer Services, when to use each, and how to choose for cost, scale, and security.", "author":{"@type":"Organization","name":"The Editorial Team"}, "publisher":{"@type":"Organization","name":"Example Tech Site"}, "mainEntityOfPage":{"@type":"WebPage","@id":"https://example.com/kubernetes-ingress-vs-load-balancer/"}, "datePublished":"2025-08-14", "dateModified":"2025-08-14", "inLanguage":"en", "isAccessibleForFree":true, "wordCount": "1400", "image":"https://example.com/images/ingress-vs-loadbalancer-diagram.png", "articleSection":[ "Definitions","How it works","Trade-offs","Evaluation","Use cases","Migration","Pricing","FAQ" ] } </script>
Accessibility checklist
- Descriptive link text (no “click here”).
- Alt text included for the diagram.
- Don’t rely on color alone for meaning. See WCAG 2.2 principles (POUR). W3C
About this guide
This guide follows the site’s promise: clear explanations → verified testing → practical recommendations. Testing summarized here used managed Kubernetes in a major cloud (HTTP routing via NGINX Ingress; L4 exposure via LoadBalancer), with the editorial team validating behavior against official docs. See How we test and Editorial standards for methods and independence.